Setting up Apache Ignite
This section shows how Ignite uses the encryption algorithm and a keystore to ensure data security.
Among the other parameters in the Ignite keystore, it also stores database parameters. These database parameters triggers the Ignite server to retrieve the encryption algorithm initialiser and its properties.
The following is the default initialiser and keystore password:
- Initialiser for setting the encryption algorithm - Waz7G611E%+6291Tqz
This initialiser encrypts the cache data. It is stored only in the database in the table
TAFJ_CACHE_KS_INITand is mandatory for Ignite. - The default keystore password - 3jyh?=%_baT
If you want to use this keystore password on the Windows command line, then you must skip the % character (3jyh?=%%_baTO).
You need to change the initialiser, keystore password and database parameters values based on the target database that exists in the keystore. For more information, see Manipulating the cachestore.keystore file.
Reading Properties from a Database
In production mode, you can get the properties from the database by default and the properties are created in the database automatically, if not available. The default configuration key is cache.configuration.
Start Ignite servers along with your application server with the following system property.
-Dcache.configuration=(my_config_id)
Reading Properties from a File
The Ignite configuration file is read from the classpath and is located in the TAFJCache.jar file. You can also specify the Ignite configuration file in the caching.properties file by using the temn.cache.ignite.conf.file.loc property. The caching.properties file is located in the $TAFJ_HOME/conf/cache directory.
The example below illustrates the Ignite configuration file in the caching.properties file.
temn.cache.ignite.conf.file.loc=<tafj.home>/conf/cache/ignite-cache.xml
For a standalone setup, the following JARs are required in TAFJ_HOME/ext/Ignite. You can also reference these JARs by the application server classpath if running in an application server context.
| Group | JARs |
|---|---|
|
org.apache.ignite |
|
|
Ignite-indexing |
|
|
Ignite-jta |
|
|
ignite-kafka |
|
|
ignite-spring |
|
Starting an Ignite Server Node
To start and Ignite server node,
- Open command line and run $TAFJ_HOME/bin/StartIgnite.
- Enter the keystore password. The default keystore password is 3jyh?=%_baT.
Setting the classpath
In order to use Ignite with JBoss and other application servers, you must correctly set the classpath to the Ignite libraries using the following procedure.
- For JBoss application server, download and copy the Ignite JARs specified in the Required Ignite JARs section.
- Reference the JARs in module.xml as shown below.
<resource-root path="./ext/Ignite/ignite-core-2.0.0.jar"/>
<resource-root path="./ext/Ignite/ignite-shmem-2.0.0.jar"/>
<resource-root path="./ext/Ignite/ignite-log4j2-2.0.0.jar"/>
<resource-root path="./ext/Ignite/ignite-spring/ignite-spring-2.0.0.jar"/>
<resource-root path="./ext/Ignite/ignite-spring/commons-logging-1.1.1.jar"/>
<resource-root path="./ext/Ignite/ignite-spring/spring-aop-4.3.7.RELEASE.jar"/>
<resource-root path="./ext/Ignite/ignite-spring/spring-beans-4.3.7.RELEASE.jar"/>
<resource-root path="./ext/Ignite/ignite-spring/spring-context-4.3.7.RELEASE.jar"/>
<resource-root path="./ext/Ignite/ignite-spring/spring-core-4.3.7.RELEASE.jar"/>
<resource-root path="./ext/Ignite/ignite-spring/spring-expression-4.3.7.RELEASE.jar"/>
<resource-root path="./ext/Ignite/ignite-spring/spring-jdbc-4.3.7.RELEASE.jar"/>
<resource-root path="./ext/Ignite/ignite-spring/spring-tx-4.3.7.RELEASE.jar"/>
<resource-root path="./ext/Ignite/ignite-spring/spring-tx-4.3.7.RELEASE.jar"/>
<dependencies>
<module name="sun.jdk" export="true" >
<imports>
<include path="sun/misc/Unsafe" />
</imports>
</module>
</dependencies>
Likewise, if you are using WebLogic or WebSphere application server, set the appropriate JARs to the classpath.
TAFJ Caching Security
The flowchart below describes the TAFJ Caching security. It shows how properties are loaded, how the keystore is accessed, and how user password must match. It does not describe the white-listing process.
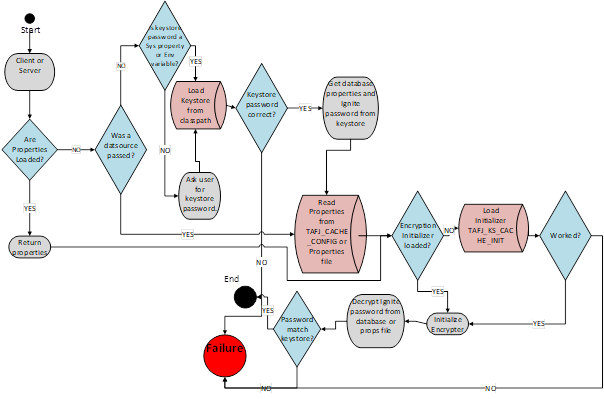
Apache Ignite does not ship with security by default, so Temenos has added its own. Caching properties are read or written from a database or the caching.properties file.
The nodes that are joining the cluster must provide a keystore password. Once the keystore is securely accessed, the node is authenticated by
- IP address (independent of Apache Ignite’s IP checking)
- An unencrypted password stored in a java keystore. This unencrypted password is matched against an encrypted password, which is present in either the database or caching.properties file.
Database connection properties are stored in the java keystore.
The starting point of a node is authenticated by the property temn.cache.ignite.allowed.ips. The node starting must be an IP recognized in one of these properties. Ignite has its own IP checking, but this is an added security. For example,
temn.cache.ignite.allowed.ips=10.41.5.51
So, the above IP 10.41.5.51 is allowed to be part of the Ignite grid. If the properties are in the database, then the database must be updated using the following commands:
SQL> update TAFJ_CACHE_CONFIG set property_value = '10.30.200.74,10.30.200.75' where property_key = ' temn.cache.ignite.allowed.ips';
SQL> commit;
An Ignite user password is stored in the keystore file $TAFJ_HOME/conf/cache/cachestore.keystore. When a node starts, the initial password is encrypted on disk in the $TAFJ_HOME/conf/cache/caching.properties file or database and compared against the password in the cachestore.keystore file.
The caching framework decrypts the Ignite user password by using an initialiser. This initialiser is retrieved from the database because the database has the ability to encrypt tables and tablespaces to provide another layer of security. To find out how to encrypt a table please see your specific database documentation. If no data is found in the TAFJ_CACHE_KS_INIT table, then there will be a security exception. The caching framework tries to speak with the database through the Temenos Transact datasource.
temn.tafj.jdbc.url=
temn.tafj.jdbc.driver=
temn.tafj.jdbc.username=
temn.tafj.jdbc.password=
The above properties are only used in a standalone mode, when you are outside the application server context.
The String values (not keys) in all the Ignite caches are encrypted with the encryption algorithm. This encryption algorithm is stored in the cachestore.keystore file with the key temn.tafj.cache.ignite.encryption.algo. The value of this key is the encryption algorithm that will be used for encrypting data in the caches and to decrypt the Ignite user password. The initialiser for the encryption algorithm is stored in the Temenos Transact database in the table TAFJ_CACHE_KS_INIT.
You can encrypt the cache data with objects as well. Not all objects and fields are encrypted due to the overhead involved. You can control the encryption of objects by using the temn.cache.encrypt.objects.stringtypes property. On setting this property to true, it will encrypt the object fields going in and out of the cache. To encrypt an object field, the object must implement the com.temenos.tafj.cache.models.Encrypted interface and annotate the fields that should be encrypted (only char[], byte[], and String types are allowed). For example:
public class TemenosDataEvent implements Encrypted {
@Encrypt
private byte[] eventData = null;
etc
}
The field eventData will be encrypted because it is annotated. Other fields will not be encrypted. Once an object is placed into the cache, its annotated fields will be encrypted. You can query an object’s state by calling the method isEncrypted(). Similarly, to decrypt an object, you can call the method get(key).
If the cache being written to is write-through or write-behind, the data going to the database will not be encrypted. It is the job of the database to encrypt data. If a cachestore writes to a database, it must consider that the data inside the cache is encrypted before it is written to the database and decrypt it.
This section shows you how to create a default keystore file for Ignite that will work with a particular database.
Run the following command where h2default-keystore.txt is the default keystore file:
%TAFJ_HOME%\bin\tKeyStore -keystoretype JCEKS -keystorepassword 3jyh?=%%_baT -file .\cachestore.keystore -sourcefile .\h2default-keystore.txt
The above command generates cachestore.keystore in the current directory with H2 database as a target and can be used to overwrite the keystore available in TAFJCache.jar.
ignite=aseiqH197%2
temn.tafj.cache.ignite.encryption.algo=AES
temn.tafj.jdbc.password=t24
temn.tafj.jdbc.username=t24
temn.tafj.jdbc.url=jdbc:h2:tcp://localhost/DEV;MVCC=TRUE;DB_CLOSE_ON_EXIT=FALSE;MODE=Oracle;TRACE_LEVEL_FILE=0;TRACE_LEVEL_SYSTEM_OUT=0;FILE_LOCK=NO;IFEXISTS=TRUE;CACHE_SIZE=131072
temn.tafj.jdbc.driver=org.h2.Driver
This section shows you how to change the encryption algo, Ignite password, or any other information that is available in the cachestore.keystore file using the following procedure.
- Create the default file by using the following command (note that % escapes % character for Windows as shown below):
tKeyStore -keystoretype JCEKS -keystorepassword 3jyh?=%%_baT -key Ignite -value aseiqH197%%2 -initialiser Waz7G611E%%+6291Tqz –file (path_to_the_file_that_you_want_to_create)
If the security provider is IBM JDK and you receive the java.security.NoSuchAlgorithmException: PBE SecretKeyFactory not available exception, then you will have to download the library for IBM JDK or change the security provider to Sun. - Add or change the JDBC password by using the following command (If the keystore doesn’t exist it will be created):
tKeyStore -keystoretype JCEKS -file C:\data\cachestore.keystore -keystorepassword my_password -key temn.tafj.jdbc.password –value my_jdbc_password
- Repeat step 2 for the following properties:
- temn.tafj.jdbc.username
- temn.tafj.jdbc.url
- Add or change the Ignite user and password by using the following command (If the keystore doesn’t exist it will be created):
tKeyStore -keystoretype JCEKS -file C:\data\cachestore.keystore -keystorepassword my_password -key Ignite -value Ignite_Password
- Add or change the encryption algorithm by using the following command (valid values are AES, DES, DES3, RC2 and BLOWFISH):
tKeyStore -keystoretype JCEKS -file C:\data\cachestore.keystore -keystorepassword my_password -key temn.tafj.cache.ignite.encryption.algo -value AES
- Encrypt a keystore or Ignite password to use in caching.properties by using the following command:
tKeyStore –algo AES –initialiser myinitialiser12345 –value Ignite_Password
The value will be encrypted and then converted to a Base64 value. The encrypted value of Ignite password is P9RdygoUjPryZBo/urbd8A==
- Read your modified keystore by using the Java’s keytool. You will get the output similar to the following:
keytool -list -storetype JCEKS -keystore $TAFJ_HOME/conf/cache/cachestore.keystore
Enter keystore password:
Keystore type: JCEKS
Keystore provider: SunJCE
Your keystore contains 2 entries
temn.tafj.cache.ignite.encryption.algo, Feb 7, 2017, SecretKeyEntry,
ignite, Feb 7, 2017, SecretKeyEntry,
Retrieving Ignite Logs
Ignite creates its own logging object. You can retrieve ignite logs using the following procedure.
- Copy the ignite-log4j2-(version).jar file to the $TAFJ_HOME/ext directory.
- Add the ignite-log4j2-(version).jar file in the classpath. This will help application servers to retrieve specific Ignite logs.
- Set up an Ignite appender in $TAFJ_HOME/conf/TAFJTrace.properties to control the log level.
JBOSS Specific Things to Do for Write-through Caching
As of now, TAFJ only supports non-transactional write-behind caching (only for Ignite) and read caching as there are issues with data consistency and querying the grid with synchronous write-through caching which are slated to be fixed in version 2.4. If you are using JBoss with write-through caches (which are always near caches in Ignite and exist in the same JVM as of this writing) and you want to use the datasource within the application server (necessary if you want your writes to exist in the same JTA transaction), then you must make the datasource global as Ignite threads need a reference to it.
<subsystem xmlns="urn:jboss:domain:naming:2.0">
<remote-naming/>
<bindings>
<lookup name="java:global/jdbc/t24DS" lookup="java:/jdbc/t24DS" />
</bindings>
</subsystem>
After you make the datasource global in standalone-full.xml, you need to set the below property in caching.properties so that Ignite threads within the JBoss JVM can use the appserver datasource.
temn.tafj.cache.datasource=java:global/jdbc/t24DS
Also, Ignite JTA jars are necessary if you want to enlist Ignite with the appserver JTA processor. The following JARs are required in the module.xml file for TAFJ to run Ignite:
<resource-root path="/ext/Ignite/ignite-core-2.1.0.jar"/>
<resource-root path="/ext/Ignite/ignite-shmem-1.0.0.jar"/>
<resource-root path="/ext/Ignite/ignite-log4j2-2.1.0.jar"/>
<resource-root path="/ext/Ignite/ignite-spring/ignite-spring-2.1.0.jar"/>
<resource-root path="/ext/Ignite/ignite-spring/commons-logging-1.1.1.jar"/>
<resource-root path="/ext/Ignite/ignite-spring/spring-aop-4.3.7.RELEASE.jar"/>
<resource-root path="/ext/Ignite/ignite-spring/spring-beans-4.3.7.RELEASE.jar"/>
<resource-root path="/ext/Ignite/ignite-spring/spring-context-4.3.7.RELEASE.jar"/>
<resource-root path="/ext/Ignite/ignite-spring/spring-core-4.3.7.RELEASE.jar"/>
<resource-root path="/ext/Ignite/ignite-spring/spring-expression-4.3.7.RELEASE.jar"/>
<resource-root path="/ext/Ignite/ignite-spring/spring-jdbc-4.3.7.RELEASE.jar"/>
<resource-root path="/ext/Ignite/ignite-spring/spring-tx-4.3.7.RELEASE.jar"/>
<resource-root path="/ext/Ignite/ignite-spring/spring-tx-4.3.7.RELEASE.jar"/>
<resource-root path="/ext/Ignite/ignite-jta/ignite-jta-2.1.0.jar"/>
In this topic