Configuring JBC and Java APIs
This section helps you with the configuration of JBC and Java APIs. JBC APIs are interface to access Sign and Verify features from an Infobasic program by using CALLJ, whereas Java APIs are interface to access Sign and Verify features from a Java program.
Configuring a JBC API
You can configure a JBC API using the following procedure.
- Copy all the dependency JARs from TAFJHome\3rdParty\integrity to TAFJHome\lib.
- Edit the keystore.properties file, which is available under resource/conf folder in TemenosSecurityWeb.war.
If the keystore is available as a physical file in the machine, then provide the path in the temn.keystore.location property . You can specify multiple paths separated by commas (,).
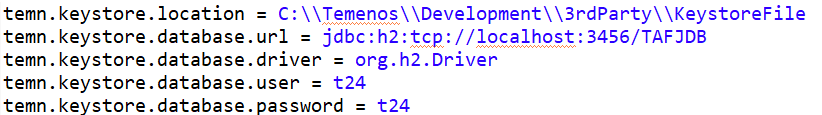
If the keystore is available in database, then specify the following properties:
- temn.keystore.database.url
- temn.keystore.database.driver
- temn.keystore.database.user
- temn.keystore.database.password
The keystore is read from the database, only when the location is not provided. - Use CALLJ to access the Sign API from JBC. To perform this step, you need to use com.temenos.security.jbc.Integrity as package.class to access the sign method as shown in the following sample request:
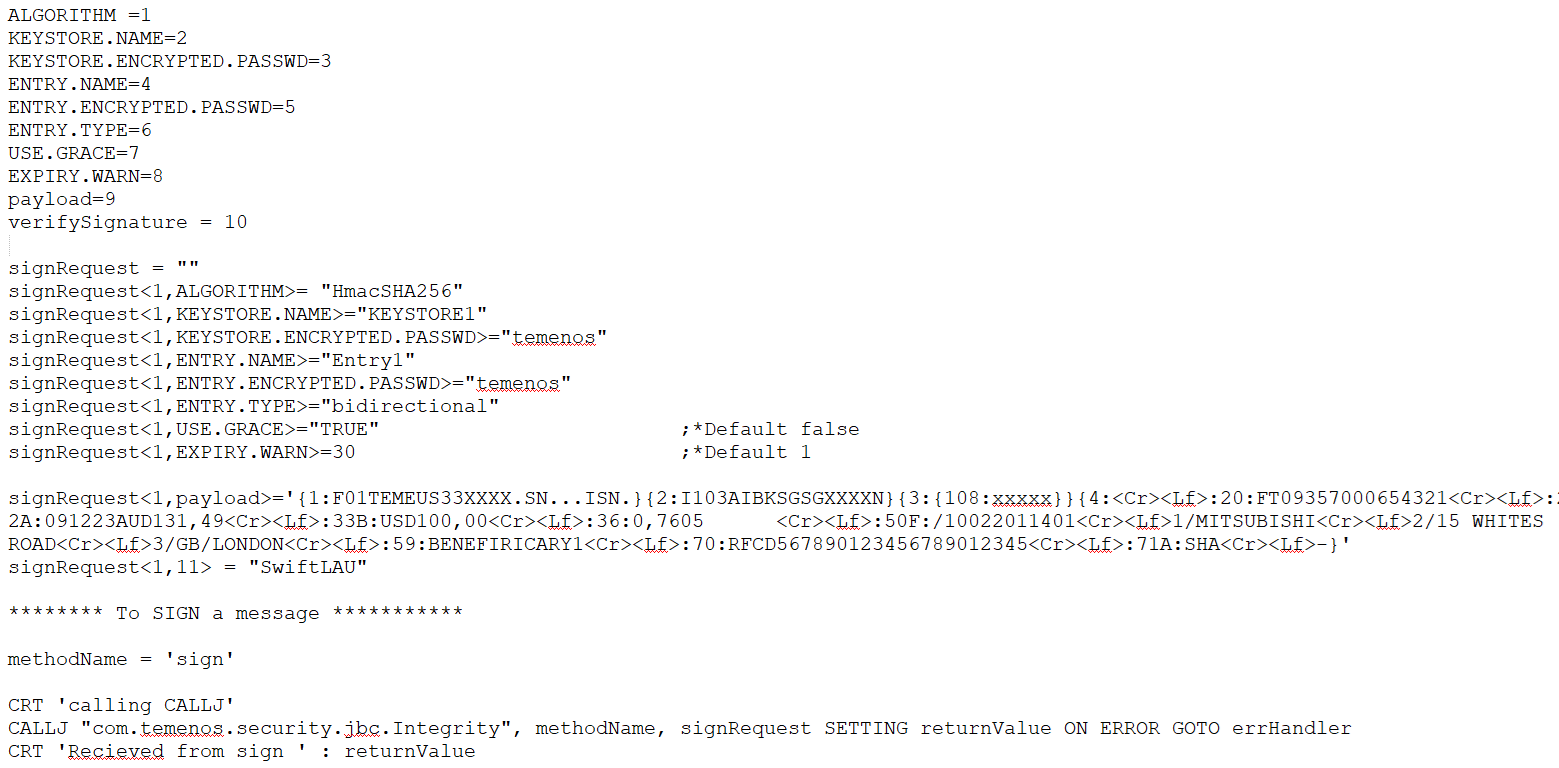
- Specify the message type at <1,12> and the digest algorithm at <1,13>. The message can be classified as XML type as shown below. SHA1, SHA256, SHA512 are supported digest algorithms. In case, if the digest algorithm is not set, then SHA1 is used as default algorithm. If the message is classified as XML, then the <signature> element is added to the actual message and provided as output for the Sign API.
signRequest<1,12> = "XML" ;*Message Type signRequest<1,13> = "SHA256" ;* Digest Algorithm
- Use CALLJ to access the Verify API from JBC. To perform this step, you need to use com.temenos.security.jbc.Integrity as package.class to access the verify method as shown in the following sample request:
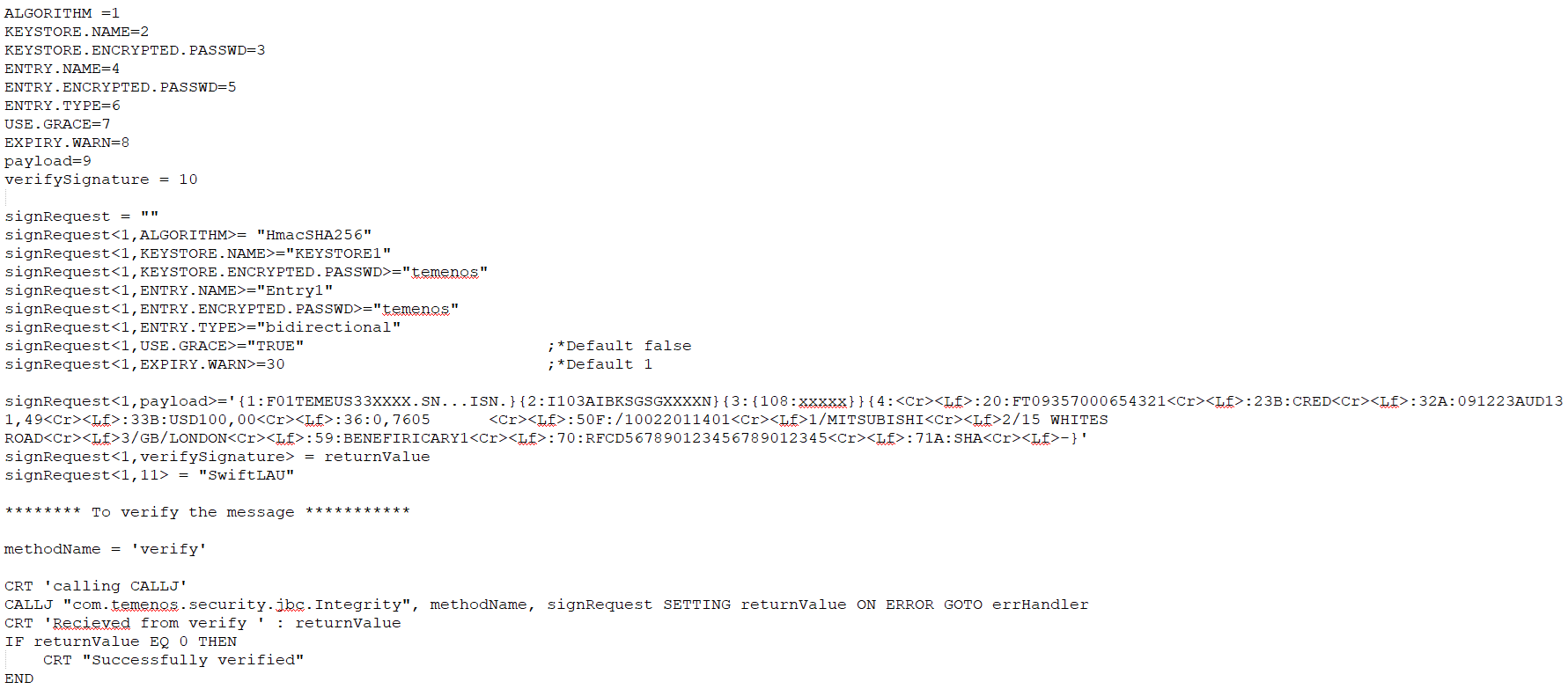
- Set the message type as XML to verify the message signed as XML as shown below. Here, the message with the <signature> element should be available at <1,9>.
signRequest<1,payload>=returnValue signRequest<1,12> = "XML" ;*Message Type
Signature algorithm is required to create and verify signature. Additionally, Digest algorithm is required for XML signature.
Following are the supported Digest algorithms.
- SHA1 (Default)
- SHA256
- SHA512
Following are the supported Signature algorithms.
|
Message Type |
For Asymmetric Key |
For Symmetric Key |
|---|---|---|
|
TEXT
|
|
|
|
XML
|
|
|
Support for HMAC-SHA224 and RSA-SHA224 is available from JAVA 1.8.0_231 and above.
SYSTEM(0) holds the errors for CALLJ. The following table shows the error codes that are specific to Message Integrity.
| Error Number | Description |
|---|---|
|
-1 |
Keystore does not exist or incorrect password |
|
-2 |
Invalid keystore password |
|
-3 |
Entry not found |
|
-4 |
Invalid entry password |
|
-5 |
All entries expired |
|
-6 |
Invalid request |
|
-7 |
Verification failed |
|
-8 |
Algorithm not supported |
|
-9 |
Configuration not found |
|
-10 |
SQL or Database error |
Configuring a Java API
Procedure
- Add the TemenosSecurity.jar file and the dependency libraries available at $TAFJ_HOME\3rdParty\integrity in the classpath.
- Edit the KeyConfig.json file in TemenosSecurity.jar/conf with the key that needs to be used for sign or verify operation.
COMPLAINCE: It can be set SwiftLAU to get the signature as a HEX 64 bytes value.
USE.GRACE: If it is set to TRUE, then the key is valid for the GRACE DAYS registered in Keystore.
WARN.EXPIRY: It describes when onward expiry warning should be notified in SECURITY.log. If it is 30, then the warning message is started to log 30 days before the key expire date until the key expires.
DIGEST.ALGORITHM: It sets the algorithm to be used to generate digest for the XML type messages. SHA1, SHA256, SHA512 are supported algorithms. In case if it is not set, SHA1 is used as default algorithm.
{
"ConfId1":
{
"ALGORITHM":"HmacSHA256",
"DIGEST.ALGORITHM":"SHA256",
"COMPLAINCE":"SwiftLAU",
"Entries":[
{"KEYSTORE.NAME":"TESTKEYSTORE",
"KEYSTORE.ENCRYPTED.PASSWORD":"temenos",
"ENTRY.NAME":"testalias1",
"ENTRY.ENCRYPTED.PASSWORD":"temenos",
"ENTRY.TYPE":"bidirectional",
"USED.FOR":[
{"OPERATION":"sign","USE.GRACE":"FALSE"},
{"OPERATION":"verify","USE.GRACE":"FALSE"}
]
},
{"KEYSTORE.NAME":"TESTKEYSTORE",
"KEYSTORE.ENCRYPTED.PASSWORD":"temenos",
"ENTRY.NAME":"testalias2",
"ENTRY.ENCRYPTED.PASSWORD":"temenos",
"ENTRY.TYPE":"bidirectional",
"USED.FOR":[
{"OPERATION":"sign","USE.GRACE":"FALSE"},
{"OPERATION":"verify","USE.GRACE":"FALSE"}
]
}
],
"WARN.EXPIRY":30
},
"ConfId2":
{
"ALGORITHM":"SHA256withRSA",
"COMPLAINCE":"",
"Entries":[
{"KEYSTORE.NAME":"TESTKEYSTOREUNI",
"KEYSTORE.ENCRYPTED.PASSWORD":"temenos",
"ENTRY.NAME":"testalias3",
"ENTRY.ENCRYPTED.PASSWORD":"temenos",
"ENTRY.TYPE":"unidirectional",
"USED.FOR":[
{"OPERATION":"sign","USE.GRACE":"FALSE"}
]
},
{"KEYSTORE.NAME":"TESTKEYSTOREUNI",
"KEYSTORE.ENCRYPTED.PASSWORD":"temenos",
"ENTRY.NAME":"testalias4",
"ENTRY.ENCRYPTED.PASSWORD":"temenos",
"ENTRY.TYPE":"unidirectional",
"USED.FOR":[
{"OPERATION":"verify","USE.GRACE":"FALSE"}
]
}
],
"WARN.EXPIRY":30
}
}
import com.temenos.security.java.Integrity;
public class TestJavaApi {
public static void main(String[] args) {
System.out.println("test message");
Integrity obj = new Integrity();
try{
String signature = obj.sign("message","SwiftLAU");
System.out.println(signature);
String retVal = obj.verify("message","SwiftLAU",signature);
System.out.println(retVal);
} catch (Exception e){
System.out.println("Error from API " + e.getMessage());
}
//For XMLType messages, pass type as third parameter
try{
String signature = obj.sign("message","SwiftLAU", MISecurityConstants.MessageType.XML);
System.out.println(signature);
String retVal = obj.verify("message","SwiftLAU",null, MISecurityConstants.MessageType.XML);
System.out.println(retVal);
} catch (Exception e){
System.out.println("Error from API " + e.getMessage());
}
}
In this topic