One-Helm Implementation for SRMS2.0 Microservice in AKS
SRMS2.0 One-helm deployment package contains simplified deployment scripts with consolidated deployment parameters, deployment types, and databases. Only the .sh scripts are retained in the deployment packages. Single helm charts are merged into one chart.
Azure Kubernetes Service (AKS) is a managed Kubernetes service that allows you to quickly deploy and manage clusters.
This section provides steps and configurations to deploy SRMS2.0 microservice in the Azure AKS environment.
Installing Azure AKS Deployment
Before you proceed with the deployment, ensure to have the Helm and kubectl – Kubernetes command-line tool installed in the system.
To install the Azure AKS deployment,
- Unzip ms-servicerequest2-helm-mongo-pack-XXX.zip or ms-servicerequest2-helm-postgres-pack-XXX.zip
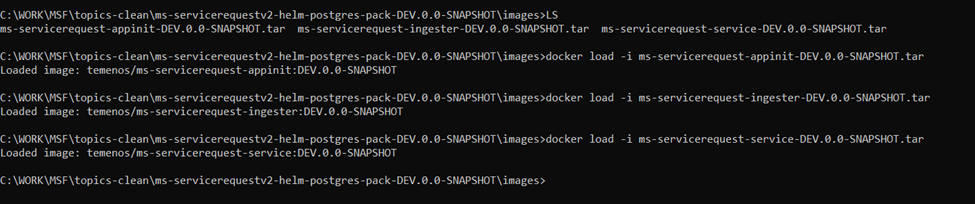
- Load the images from the local to the Docker container.
- Create a Resource Group for the Azure Kubernetes Cluster.
- Configure the Azure AKS Cluster.
- Create an Azure Container Registry (ACR) instance and tag a container image for ACR.
- Upload the image to ACR and view images in your registry.
- Create an Event hub to maintain a Kafka connection.
- Configure kubectl to connect to your AKS cluster.
- Deploy the generic config in Kubernetes. Refer One-Helm Implementation for Genericconfig Microservice in AKS to know more about the steps to deploy GeneriConfig microservice.
Pre-Installation Requirements
Refer Pre-installation Requirements section to know more about the steps required to deploy Adapter Microservice in K8 deployment.
Loading images inside Docker
To load the images inside the docker,
- Unzip ms-servicerequest2-helm-mongo-pack-XXX.zip or ms-servicerequest2-helm-postgres-pack-XXX.zip. The images for the services are available inside the unzipped pack, the images folder.
You can obtain the images saved in tar format using the docker save command (The number of tar files depends on the number of services required for the microservice). These images should be pushed into the repository.
- Load the images from ms-servicerequest2-helm-postgres-pack-XXX > Images.
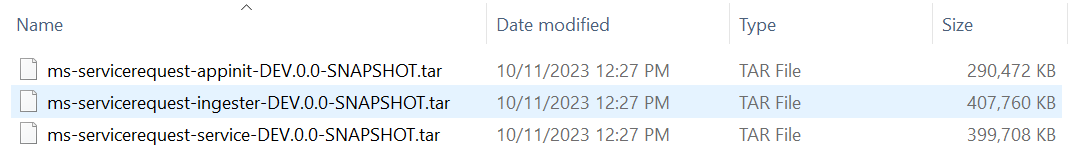
- Use the docker load command to get the images. For example, docker load --input ms-servicerequest-appinit-XXX.tar.
- Load all the images available inside the folder.
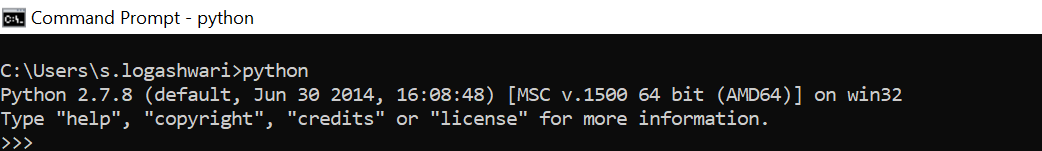
Use of .sh file in AKS folder
This file is used to create and store secret details such as User ID, its password or JWT token, and so on. If you have the python version 2.7.8 (Supported one), comment the existing line and overwrite the SP_APP_ID with the command below.
SP_APP_ID=$(az ad sp list --display-name http://${SERVICE_PRINCIPAL_NAME} --query [].appId --output tsv).
Configuring .env files for Deployment
This section covers the required configuration changes to be done for Azure AKS deployment.
This file is available in the scripts > Common folder. This file contains variables that are referred to in other .sh files. Default values are already available in this file. These are enough to create a resource group in Azure AKS. You can create a new resource group with a different name using the following configuration changes.
|
Export Variable |
Change |
|---|---|
|
SUBSCRIPTION_ID |
|
|
RESOURCE_GROUP_NAME |
|
|
AKS_CLUSTER_NAME |
|
|
AKS_NAME |
|
|
ACR_NAME |
|
|
SERVICE_PRINCIPAL_NAME |
|
|
STORAGE_ACCOUNT_NAME |
|
These files are available in Scripts > Common folder as above and any configuration to be made can be done in this files before deploying SRMS2.0 microservice in AKS.
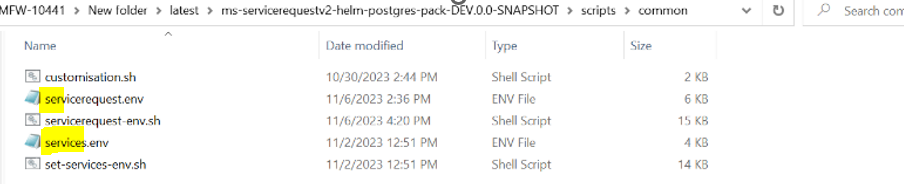
The values configured for the AKS deployment of SRMS2.0 microservice are shown in the screenshot below.
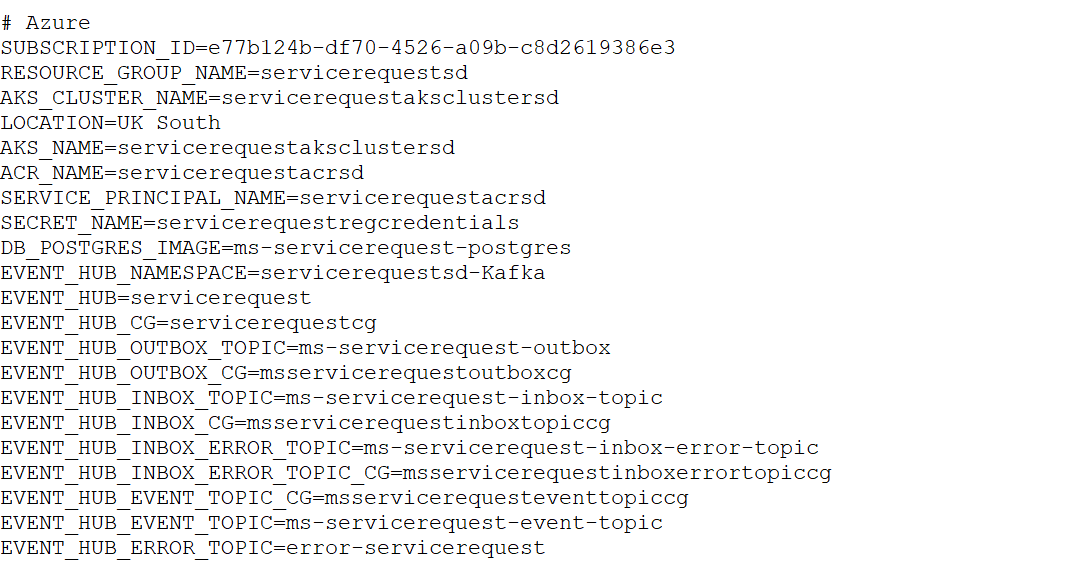
Before running the above script, configure the following files with the given values.
|
File name |
Export Variable |
Change |
|---|---|---|
|
servicerequest.env |
TAG |
|
|
services.env |
DATABASE_MONGODB_CONNECTIONSTRING |
|
|
servicerequest.env |
DATABASE_POSTGRESQL_CONNECTIONSTRING (if required to connect Postgresql Azure Db) |
|
|
servicerequest.env |
AZURE_DATABASE_POSTGRESQL_DBNAME |
|
|
servicerequest.env |
DATABASE_POSTGRESQL_USERNAME (if required to connect Postgresql Azure Db) |
|
|
servicerequest.env |
DATABASE_POSTGRESQL_PASSWORD (if required to connect Postgresql Azure Db) |
|
|
servicerequest.env |
RESOURCE_GROUP_NAME |
|
|
servicerequest.env |
AKS_CLUSTER_NAME |
|
|
servicerequest.env |
ACR_NAME |
|
|
servicerequest.env |
EVENT_HUB_NAMESPACE |
|
|
servicerequest.env |
RUNTIME_ENV |
|
|
servicerequest.env |
GC_CONFIG |
|
|
servicerequest.env |
API_KEY |
|
|
servicerequest.env |
EX_BASEPATH |
|
|
servicerequest.env |
EX_RESPATH |
|
Deployment of SRMS2.0 Service in AKS
To run the SRMS2.0 microservice in the Azure Kubernetes package,
- Open gitbash in administrator mode and navigate to ms-servicerequest2-helm-postgres -pack-XXX/ ms-servicerequest2-helm-mongo -pack-XXX > Scripts > aks. The corresponding AKS scripts that run to create required azure resources such as acr-resource-creation, acr-setup, destroy-resourcegroup, env, event-hub, event-hub-topic, secret, setup are available in Scripts/aks folder.
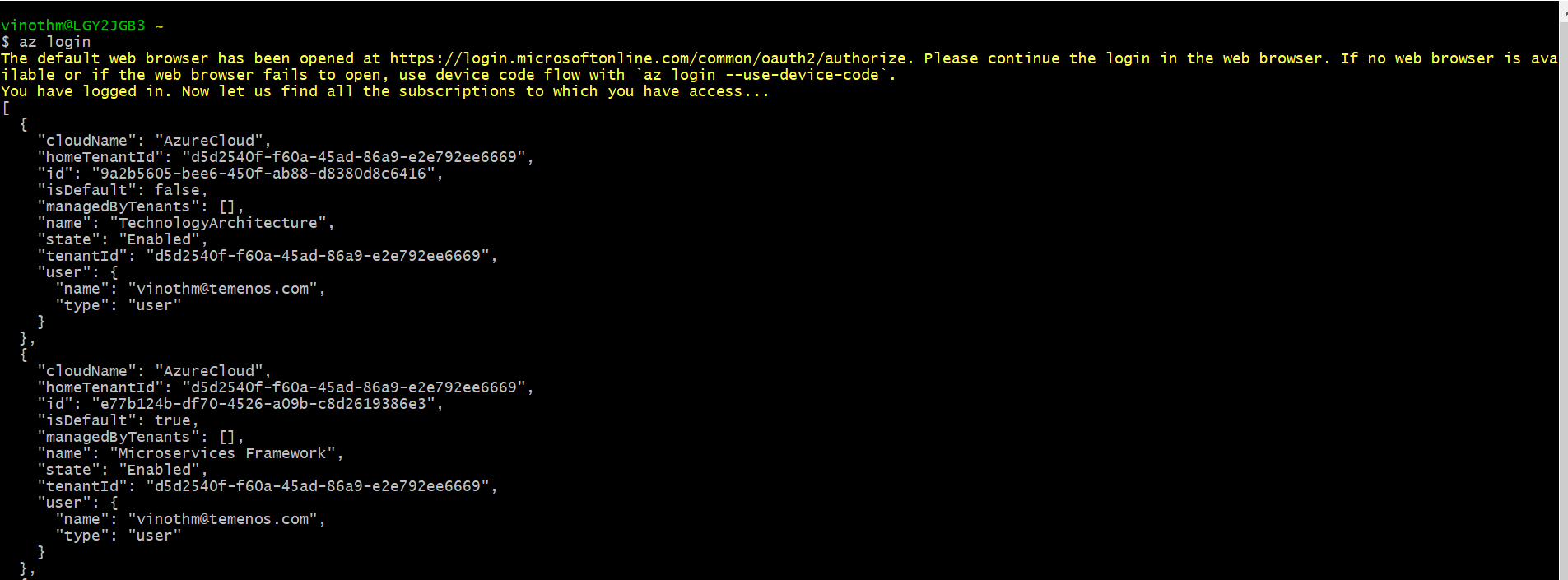
- Login into the Azure account using the az login command as shown in the screenshot below.
- Run ./destroy-resourcegroup.sh to remove the resource group, container service, and all related resources.
- Run setup.sh<dbname> to call all the shell scripts available in the .sh folder.
- For Postgresql - ./setup.sh postgresql
- For mongodb - ./setup.sh mongodb
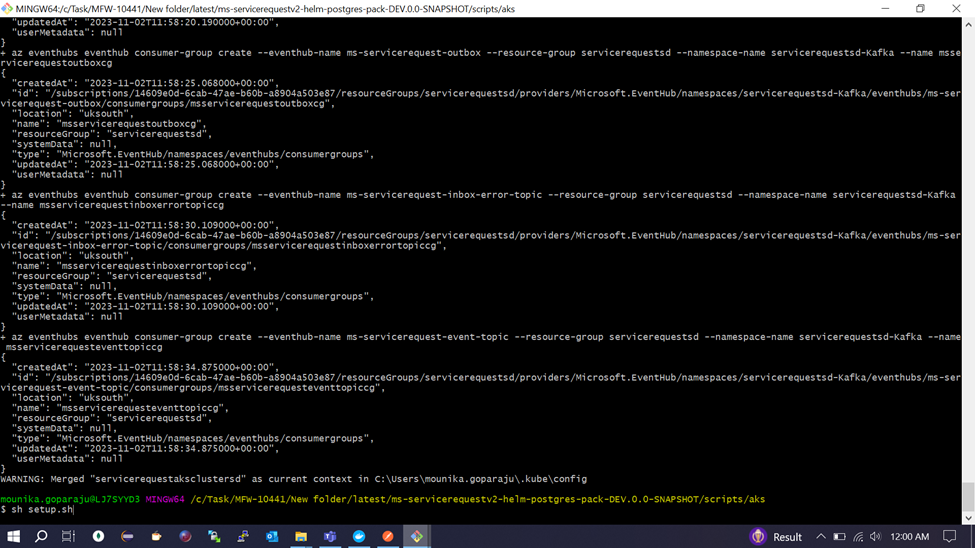
- Log in to portal.azure.com with a valid Azure login id to check the resource group created.
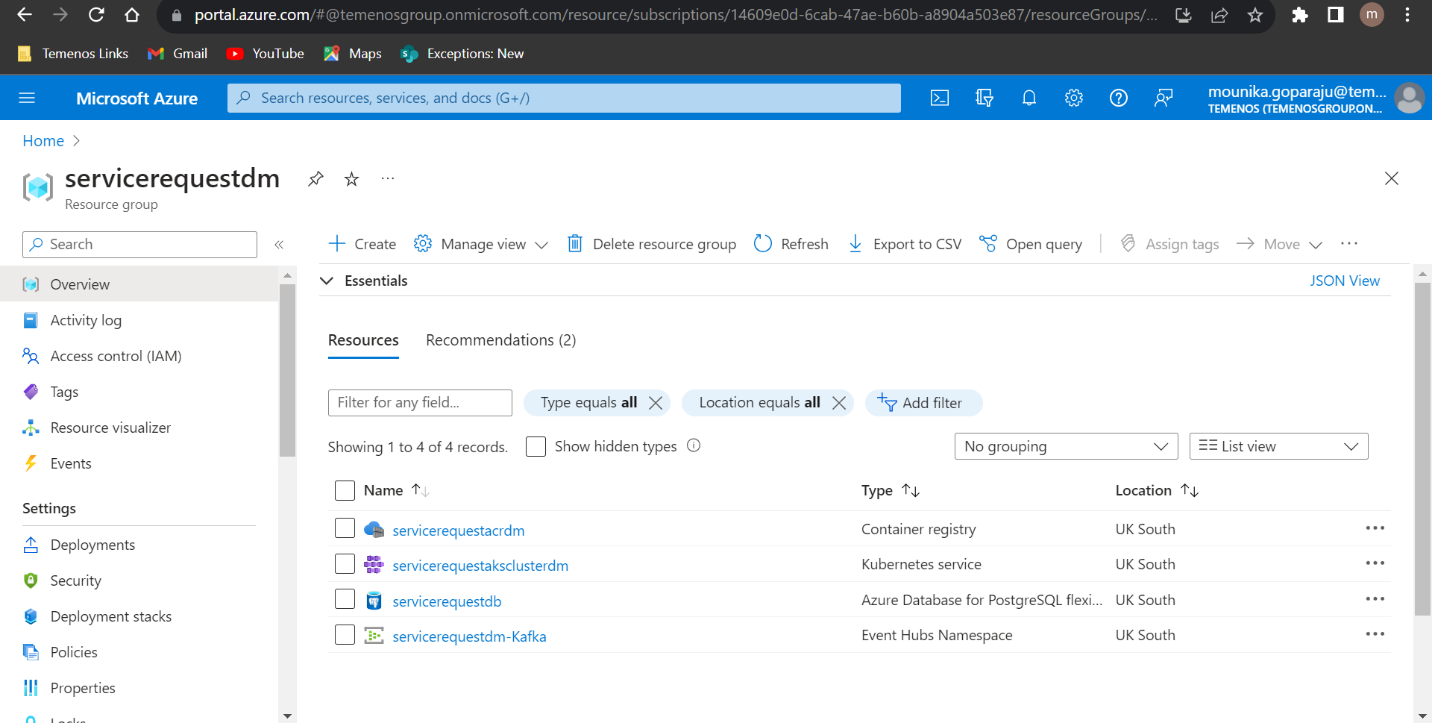
- Navigate to Resource groups from home and change the filter to all. The system displays the resource group in the list as shown in the screenshot below. A sample resource group is created with the name servicerequestsd.
- Navigate inside the Resource group folder to check whether container registry, Kubernetes service, Storage account, EventHub Namespace.
To install SRMS2.0 microservice Ms in Azure AKS, perform the following steps.
- Navigate to Scripts > aks folder. You can run the start-servicerequest.sh available in aks folder using a normal git bash prompt or any shell prompt. The SRMS2.0 microservice is up and running in AKS.
The command syntax for the deployment is ./start-servicerequest.sh <<deployment type>> <<database type>>.
For example, ./start-servicerequest.sh aks postgresql
./start-servicerequest.sh aks mongodb
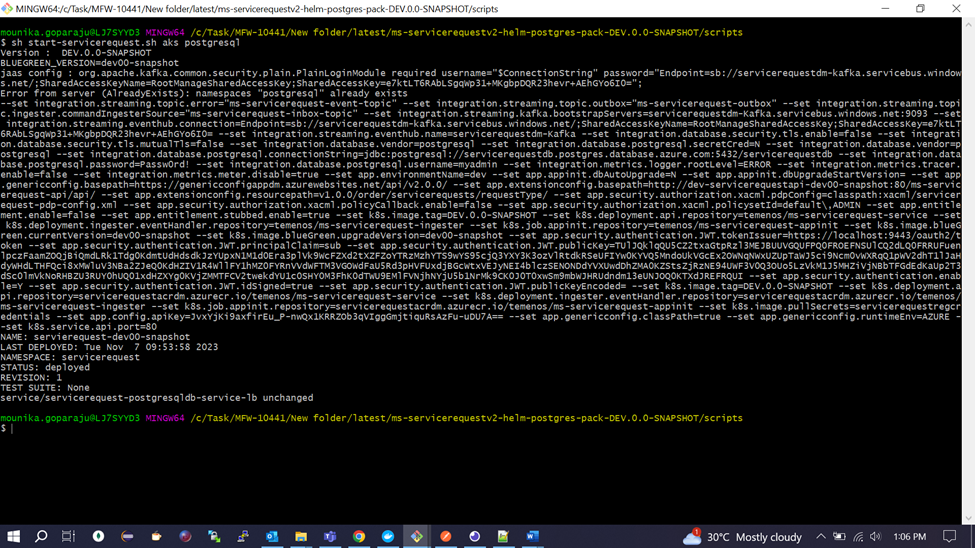
- Check whether the deployment is proper without any errors and the pods are running successfully as below.
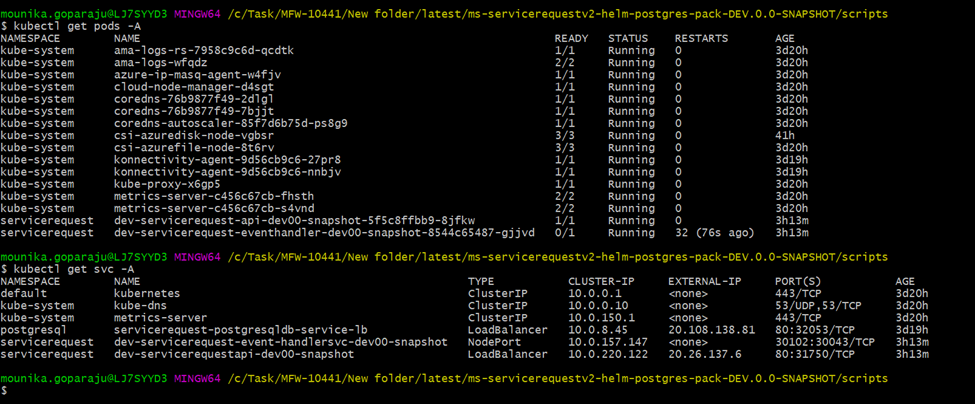
Part of the same deployment, a node port service for adapter api is created with port as 80 and public IP is exposed in External IP.
Deployment Validation
To check whether the connection is up and running, run the sample service.
POST/order/serviceRequests/serviceRequestConfiguration?requestType={requestType}
[http/https]://<<HOST_NAME>>[:<<PORT>>]/ms-servicerequest-api/api/v1.0.0/order/serviceRequests/serviceRequestConfiguration?requestType={requestType}{
"serviceRequestSchema": {
"$schema": "http://json-schema.org/draft-04/schema#",
"type": "object",
"properties": {
"accountNo": {
"type": "string",
"title": "Account Number",
"description": "Account No of the user"
},
"chequeType": {
"type": "string",
"title": "ChequeBook Type",
"description": "Type of the chequebook"
},
"notes": {
"type": "string",
"title": "Notes",
"description": "Notes"
}
},
"required": [
"accountNo",
"chequeType",
"notes"
]
},
"serviceRequestProperties": [
{
"key": "id",
"value": "CHQ"
},
{
"key": "noofapproval",
"value": "3"
}
]
}{ "serviceRequestId": "chequebook",
"message": "Service Request Type Schema Created Successfully",
"responseStatus": "Created"
}In this topic